An interesting problem that came my way in the last week:
I wanted to create a service endpoint interface inside my private cloud network to get to Crowdstrike. CrowdStrike provide comprehensive suite of endpoint protection services. Their service itself is hosted in AWS, meaning you can also connect to it using AWS private Link. This is great because it means hosts in private networks don’t’ need access to the Internet. The problem is that private link doesn’t work cross region. Crowdstrikes service is in us-west-2/1 or eu-central-1.. My environments are in neither of them.
There are two documented approaches from Crowd strike on how to solve this…
(1) You can create a Vpc in one of the service regions, and peer it to another Vpc in another region. Vpc to Vpc cross region peering is a thing and it works fine. However i’ve got many many vpcs that are connected via TransitGateways and or Cloudwan. I’d have to peer them all. ( And I’m not keen on that ). Vpc are non transitive so, you cant route traffic through them. so this by itself is’tn really Isolutin.
(b) you can create the vpc in the service region, a long with a transitgateway and then peer that TG with your TG in the region you want to operate in. Its quite a lot of infra and hassle/cost for just a one endpoint.
I’ve done (b) previously, but thought there must be a better way.
I was somewhat inspired by Ankit Chadha’s blog a few weeks ago about egress/ingress patterns. That makes use of a NLB to provide connectivity from the ‘outside’ world to a host on the inside. It seemed viable ( thanks to Andy Taylor for hearing my late night ramblings ) so I set to making this work.
What I’ve done is extend model (a) which peers two vpcs’ together, and then places a Network Load Balancer in the ‘home’ vpc. THe NLB targets the private link endpoints in the remote vpc. THen a bit of route53 action, which makes querys for the cloudsink.net domain hit the NLB, rather than the private link endpoints. And becuase this VPC is attached to my cloudwan network, all the other vpcs’ can reach it..
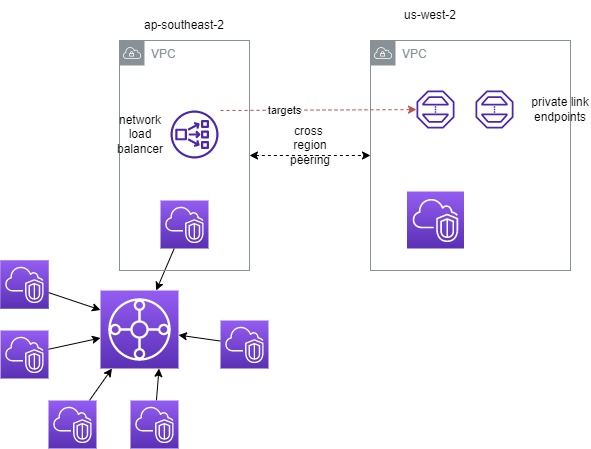
End result, is that it just works, clients dont’ need any special configuration. I dont’ have to peer lots and lots of VPC’ and i dont’ have to create a Global network with TG peering just to get a pair of endpoints! Its got quite a considerable cost saving too.
Coding this did proove to be quite a challenge. I decided to use a relatively new feature in aws-cdk which is cross region references. Its still ‘experimental’ and it most definately has some rough edges. I’ll not bore you with all that, but needless to say, its probalby not quite ready for prime-time.
I’ve coded a up a very opinionated set of constructs ( https://constructs.dev/packages/raindancers-network/v/1.15.2/api/CrowdStrikeExtendedEndpoint?lang=typescript ) which you can borrow if you want, but at this point i’ve not written any implemnetation notes for them..
I probalby will create some more general purpose constructs for this, that are not crowdstrike specific..

Leave a Reply